User Authentication and Service Communication
Kaptain uses some components of the service mesh Istio and the authservice for user authentication and traffic management purposes.
For user authentication, Kaptain uses the authservice to allow end-users to log in to the Kubeflow UI using authentication credentials. The authservice consults the OIDC provider (for example, Dex) to verify the user’s credentials and authenticate them. If not yet authenticated, the integrated, zero-trust EnvoyFilter redirects the login request to the OIDC provider for authentication. Access is granted to successfully authenticated users, if the credentials are valid, or rejected for failed login attempts. For more information on users and permissions, refer to Users and Permissions Management.
For traffic management, Kaptain uses Istio as a load balancing solution that serves HTTPS traffic to allow secure connections between service users. These service users correspond to all of Kaptain’s services, which run as a part of a service mesh, where all service-to-service connections are encrypted with a mutual TLS certificate. For this purpose, Kaptain uses a customization of the IstioOperator to install an Ingress Gateway through which all kaptain-ingress inbound and outboud HTTPS requests are routed. This is done using the default Kaptain-managed or an alternative customer-managed certificate.
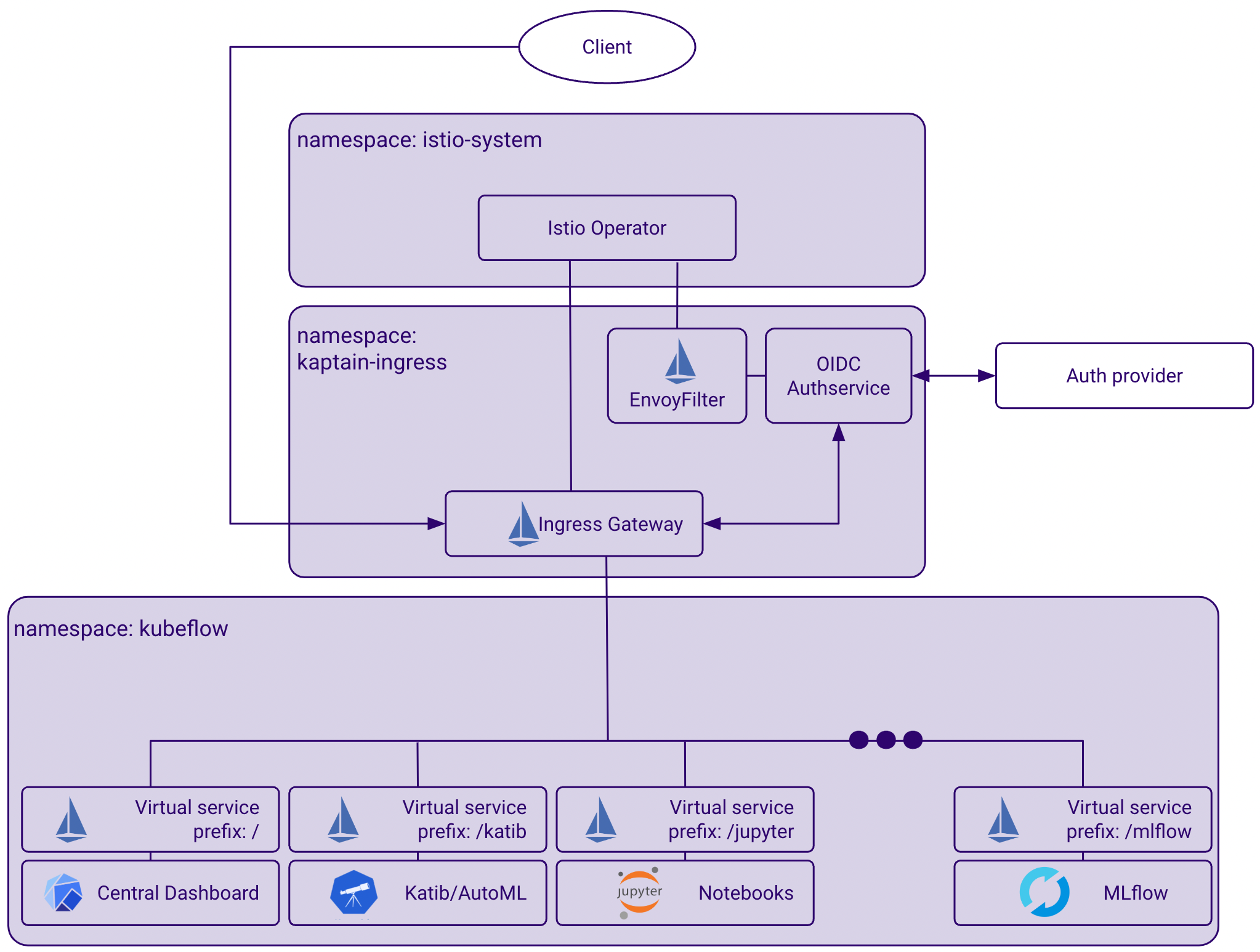
The previous diagram depicts the istio-system namespace and two other namespaces of Kaptain’s landscape, to which Istio and the authservice have access:
The
kubeflownamespace, which hosts the Kaptain UI, and other virtual services related to model training, model tracking and more.The
kaptain-ingressnamespace, which hosts services related to user management, authentication management, among other administrative tasks.
By having access to these namespaces, Istio and the authservice can provide traffic management and user authentication in Kaptain.
